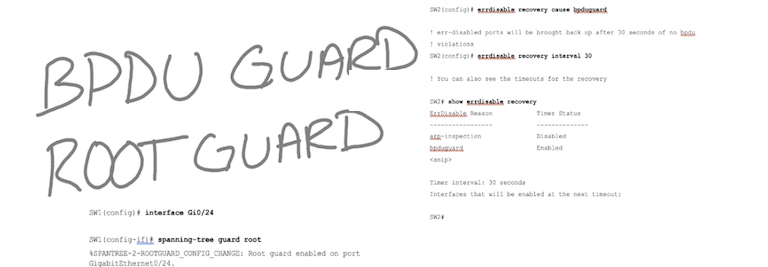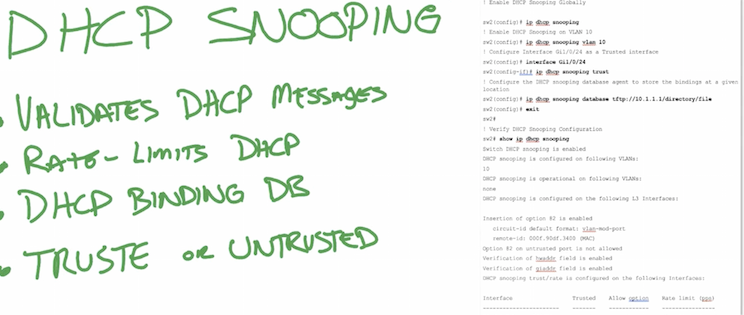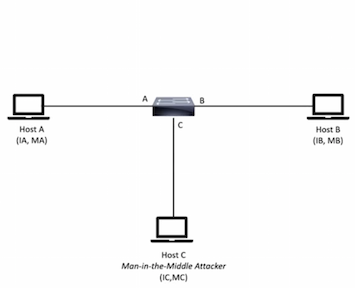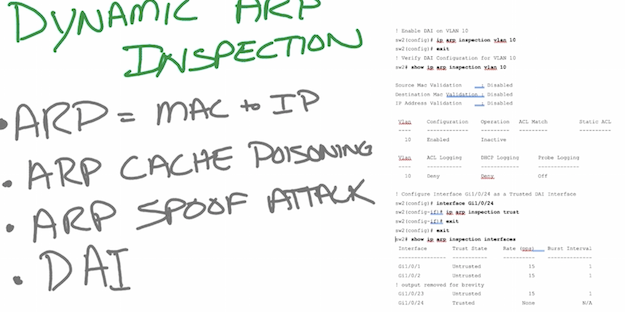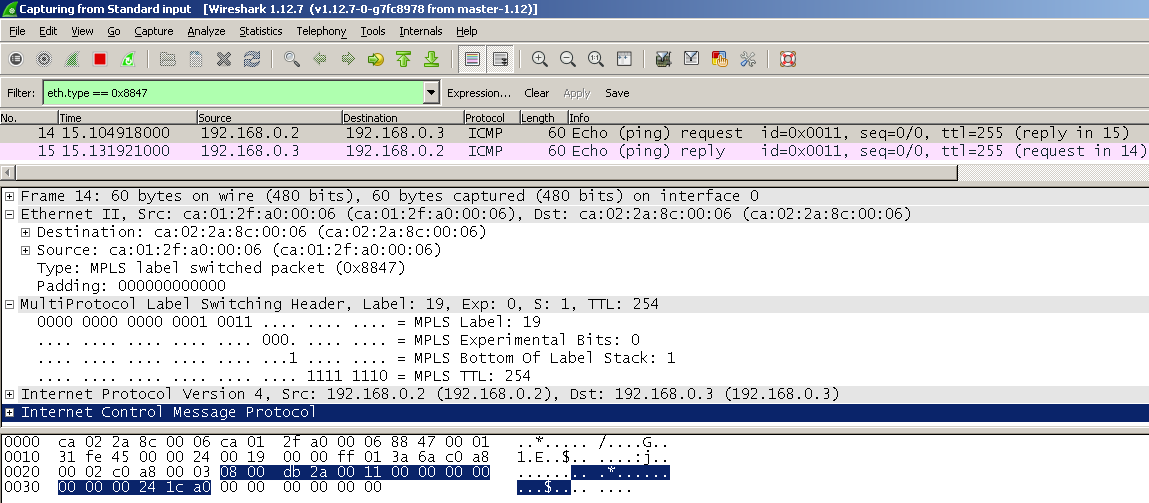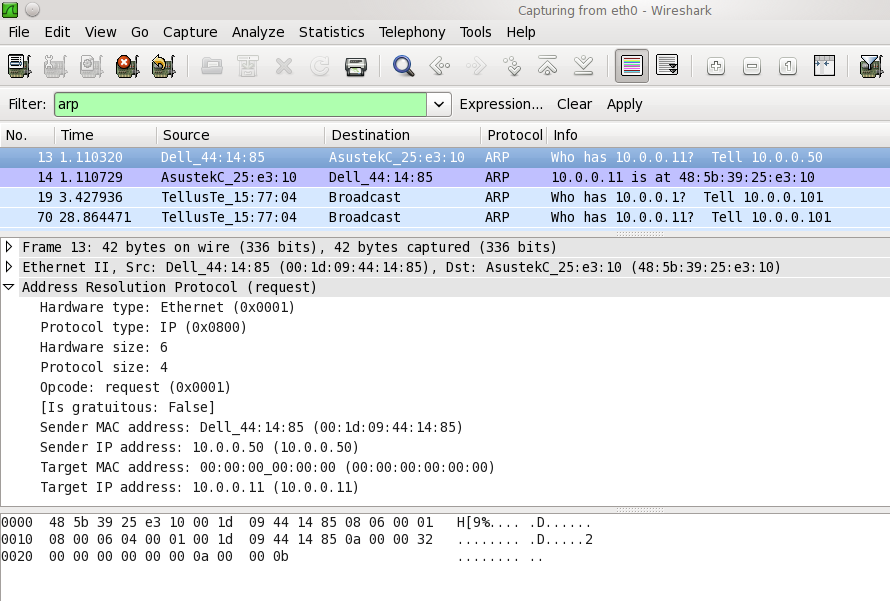
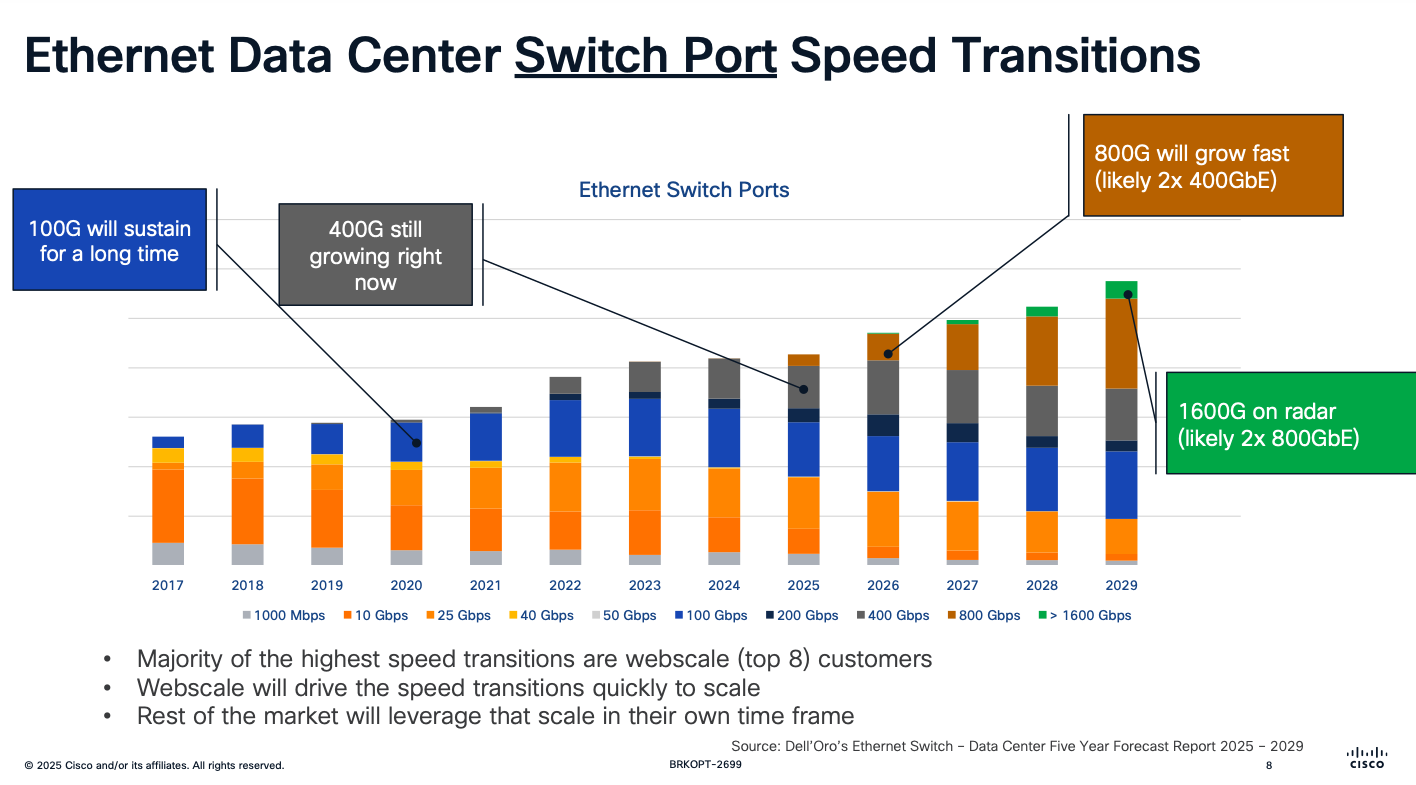
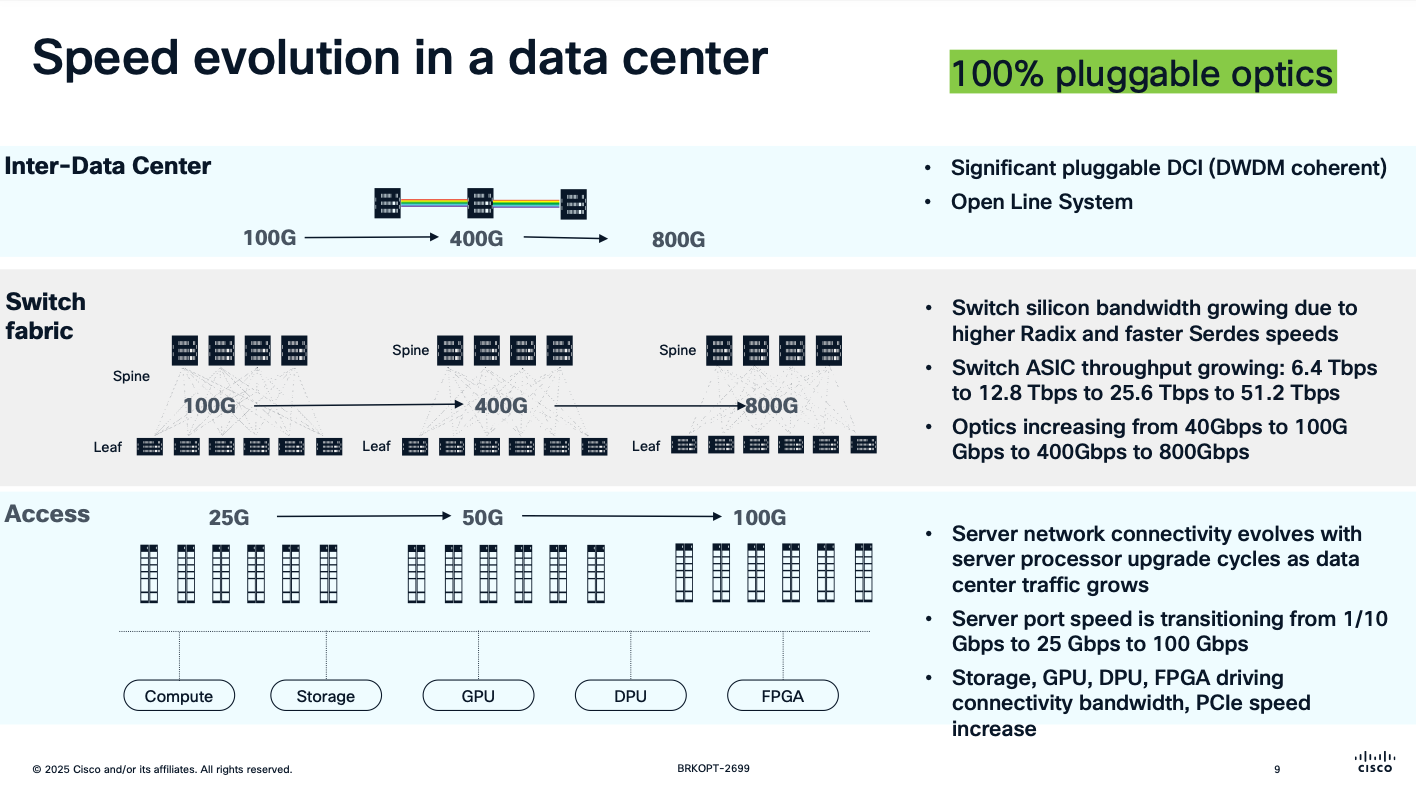
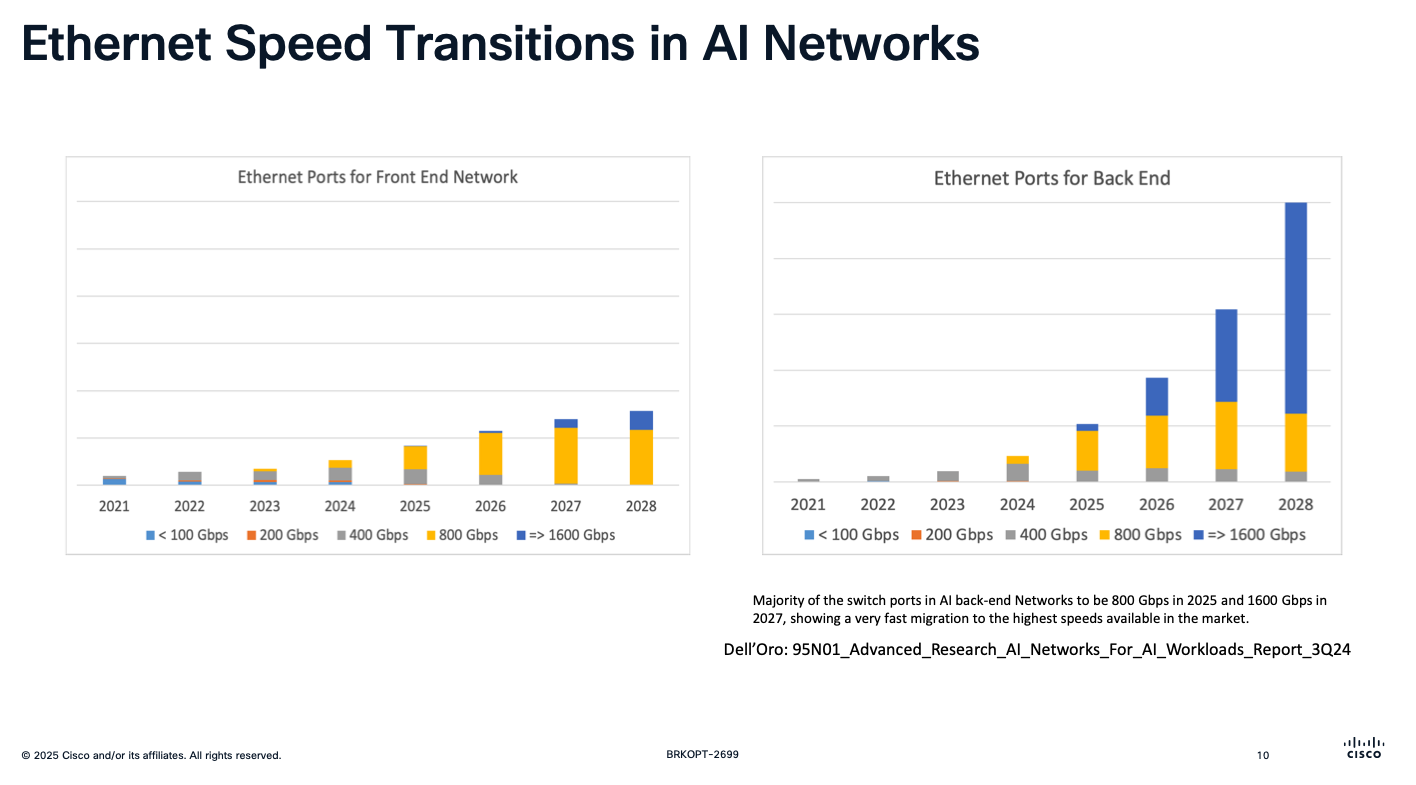
- С точки зрения физики (про оценку см. глазковые диаграммы)
- 25G достаточно «нежный» интерфейс в сравнении с 10G
- 50G еще более
- 100G – это четыре 25G (4x25G lines), причем может отваливаться один из lane независимо от других (подробнее так же в глазковые диаграммы)
- 50G – это восемь 50G (8x50G)
- Про новые модули до 800G (про 1600G / 1.6T выше) в отдельной статье SFP: НОВЫЕ МОДУЛИ SFP28 (25G), QSFP28/CFP2-4 (100G), QSFP-DD (400G-800G), OSFP (400G-800G)
- (новая информация выше) Сервера по линкам в 2021 (данные Ethernet Networking Division Intel на основе предсказания Dell):
- 50% – 10G
- 50% – over 10G
- 25G – 20%
- 50G – 20%
- 100G – 10%
- 400G NIC
- Nvidia/Mellanox ConnectX-7 (CX7)
- Broadcom Thor2
- AMD Ultra Ethernet — Pensando Pollara 400GbE
- 100G NIC
- Mellanox/NVIDIA ConnectX5, ConnectX6,
- Intel E810 (Q)SFP28
- Ростелеком активно закупает 100G магистральное оборудование (напр.
Читать дальше