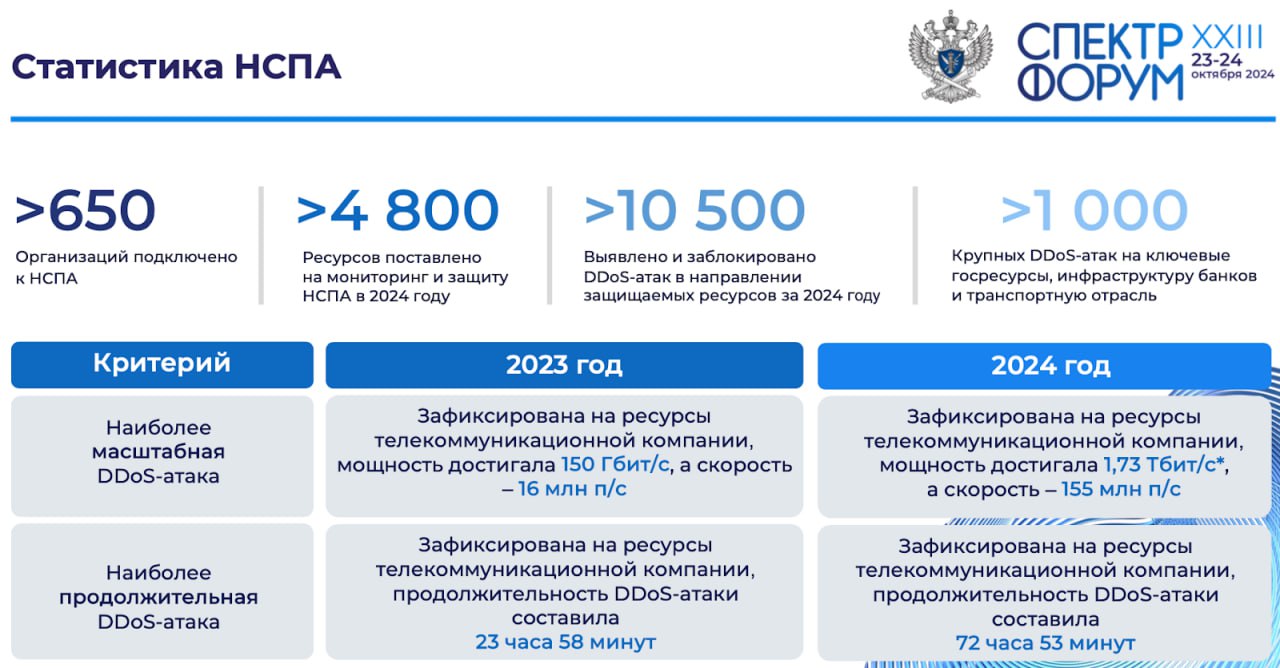
- Самые мощные атаки РФ (по миру актуальная атака на клиента CF 8 tbps в конце статьи): 150 гбит / 1.5 терабит ; 15 MPPS / 150 MPPS ; сутки / трое в 2023 / 2024 соответственно
The Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Investigation (FBI), and the Multi-State Information Sharing and Analysis Center (MS-ISAC) are releasing this joint distributed denial-of-service (DDoS) attack guidance
DOS/DDOS теория
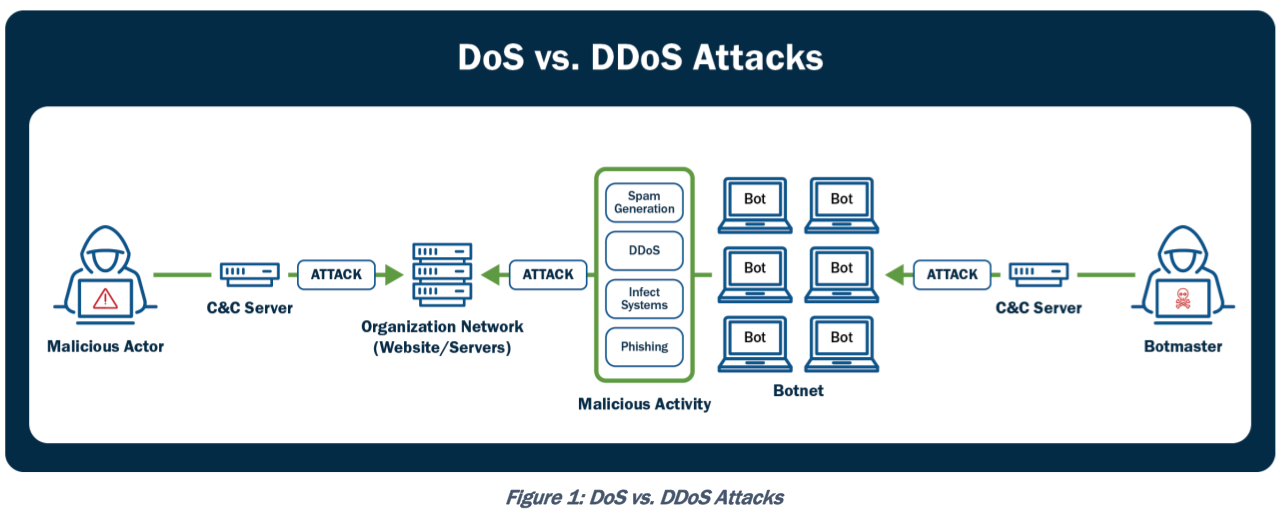
DOS/DDOS (dns lookup, half-open attacks like syn flood; ddos = dos + botnet => flood guard) – отправляем большое количество каких-либо пакетов/запросов/ответов для отказа в обслуживании сервиса из-за нехватки ресурсов (процессинговых, памяти, сетевых и проч).
Читать дальше