Layer 2 attacks
Если разрушить фундамент – разрушиться весь дом. Поэтому безопасность на канальном уровне крайне важна.
Disrupt the bottom of the wall and the top is disrupted too.
Рекомендация/технология и от чего защищает:
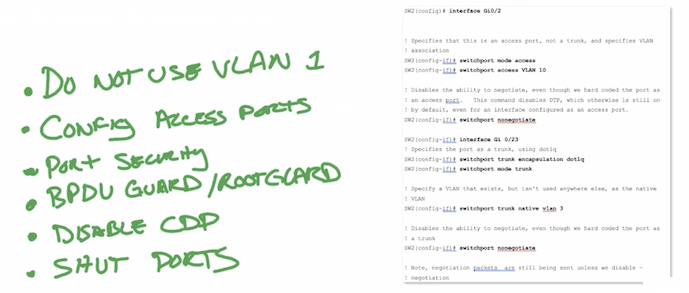
- Select native vlan as unused vlan on trunk (not vlan 1) – vlan hopping attacks
- Configure access ports as access ports – DTP attacks
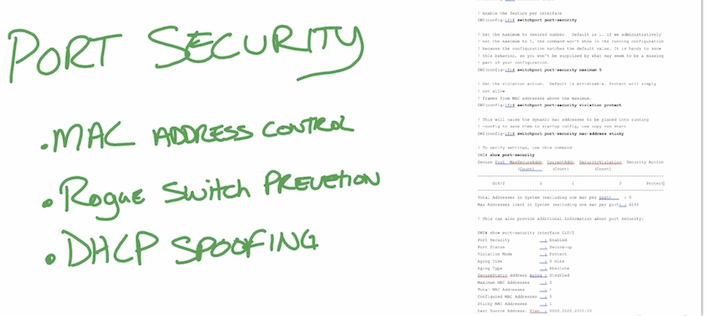
- Limit mac addresses by port security – CAM attacks, mac spoofing
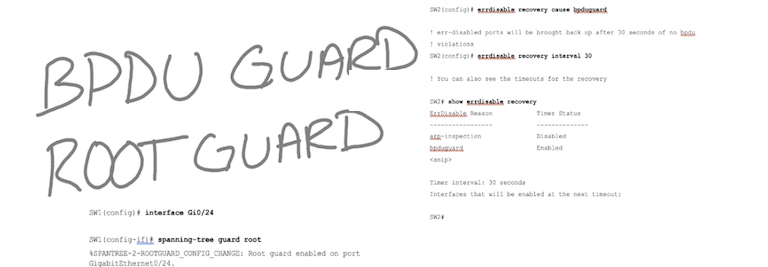
- BPDU guard/root guard – STP topology (DOS, MITM attacks)
- Disable CDP/LLDP – reconnaissance attacks

- Shut unused ports – Implicit deny/whitelisting/default deny: теория в security, пример практики в cisco ios nfp architecture
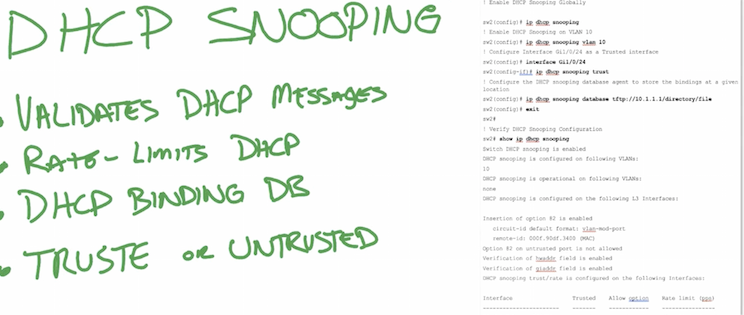
- DHCP snooping – dhcp attacks, basic for DAI/IPSG (IP source guard)
- DAI – arp spoofing attacks, rate limit
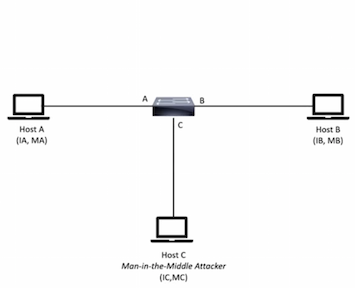
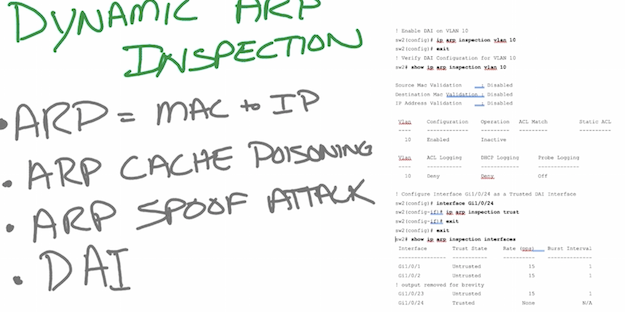
- IPSG – ip spoofing attacks
- Storm control – flood/DOS attacks
- 802.1x – authentication before access to network
- ACL – control by policy
